About Martus and Security
What is Martus?
Named after the Greek word for witness, the Martus Project provides an efficient and secure way to store and retrieve information about human rights abuses. Using the Martus application, you can create records of human rights abuses, attach supporting documents, and store the information on a secure server. Martus encrypts data directly on your computer, and sends this data in an encrypted form to a secure server when you have an internet connection. To learn more about the problems the Martus Project addresses, how Martus is being used throughout the world to securely collect and store sensitive data, and future plans for the project, visit http://benetech.org/our-programs/human-rights/.
What Martus can and can’t do
Martus can help with some digital security problems but it also has limits. You should consider vulnerabilities in work you conduct outside of Martus and identify tools that may reduce your risk.
Benefits of Martus
- Structure and standardize your data collection
- Organize and analyze your collected data
- Encrypt the data to protect others from accessing it
- Securely backup off-site which allows you to recover your data if you lose your device
Limits of Martus
- Martus does not replace direct, immediate communication. You should look into secure options such as encrypted SMS, encrypted messaging systems, secure options for email etc.
- Martus can only protect the data entered into the system, if you will be working locally in other programs (Word, Excel etc.) you should consider encrypting those files or full disk encryption.
- Martus is only as secure as your device. You should be sure to protect your device from malware as well as maintain passwords on your mobile phone and SIM.
- Martus does not enable real-time collaboration between users, like Google Docs does.
- Martus is not an efficient replacement for filesharing or syncing services like Dropbox or Google Drive.
- Martus does not allow for remote login from any computer or through a web browser. Your account’s private key must be present and the Martus desktop client must be installed on the computer you are using to access your account.
How does Martus keep the data secure?
Every Martus account has a key which can only be accessed using the password for that account. When you sign in to the Martus software, your password enables the application to open the key (associated with the MartusKeyPair.dat file,) so that you can see the records you’ve created and stored.
Your password is yours alone; without it, no one can open the records you’ve sent to the server, or any of the records on your hard drive. However, if you’ve opted to share records with a Contact, the Contact account holder will be able to see the data that you sent to the server.
Information secured with Martus is also protected from being modified by others and the software ensures that no one can create false or inaccurate records using your account. Even if your computer is lost, seized, or stolen, Martus ensures that data entered into Martus records cannot be read by those without permission to access the data.
A Martus server is a computer server that accepts encrypted records, securely backs them up, and replicates them to multiple locations, safeguarding the information from loss. (Benetech provides the server software to the organizations that host Martus servers, but it does not host Martus backup servers directly; e-mail martus@benetech.org for a list of potential server hosts.) Any records you haven’t sent to a server exist only on your computer. If your computer is lost, stolen, or damaged, you could lose all of that data. The server acts as a backup mechanism, so the data entered into Martus can be recovered if you lose access to your computer. With your key and your username and password, you can install Martus on a different computer and access all the private data in records you sent to the server. And if you have set up any Contact accounts to receive records from you, sending records to the server makes them available to those accounts.Why is Martus an open source application?
Independent programmers can review the code in an open source application in a way that they cannot in traditional applications. Benetech has developed Martus for use by human rights organizations, and it has not included any hidden means of collecting information from Martus users, or of having the application perform any hidden tasks. Because Martus is an open source application, you don’t have to take our word for it. Any organization can have the code independently verified to see that it does what we say it will do.
To learn more about open source technology, visit the Open Source Initiative at http://www.opensource.org.
Why is security so important?
The people who give you information about human rights abuses are concerned about security and privacy—and you need to be just as concerned in order to protect them and yourself.
Increasing access to technology (phones, internet, and social media) increases risks in this digital arena. Digital security has consequences for physical security.
Tools like Martus should be part of a security culture you establish and practice to keep yourself and your network safe. For more details on security culture and digital security considerations see our Digital Security PPT.
Other tools and resources that might be helpful for the security of communications and information:
- Anonymizing Internet Traffic (i.e. Tor)
- Encrypted VoiP (i.e. Jitsi)
- Encrypted Chat (i.e. Pidgin, Adium, Gibberbot, etc.)
- Encrypted Email
- Mobile apps (i.e. Obscuracam, Orbot, etc.)
- Whole Disk Encryption
Resources for learning more about digital security:
How can I be secure when using Martus?
It’s important that only the designated people have access to the records you’ve created, especially the information you deem particularly sensitive. It’s equally critical that no one else is able to modify the data you submit, or to create false or inaccurate records using your account. There are steps you can take to prevent someone from using your Martus account to read the data you’ve collected or to submit additional data, even if they steal your computer or otherwise gain access to it.
- Use a strong password
- See Creating a Strong Password, for best practices in creating strong passwords.
- Protect your login information
- Do not share your user name or password with anyone unless you absolutely need to, and you trust that person to keep that information responsibly.
- Do not keep your username or password on a post-it on your workdesk or laptop, or in a Word document on your computer.
- Keep your key safe and up to date
- Ensure an encrypted single-file backup of your key is stored somewhere safe and off your computer, and that you know the password used to access it.
- If you change your account password, be sure to create a new single-file backup of your key, and delete previous copies made.
- Ensure you have completed the multi-part backup of your key and have kept the parts separate and each in a safe place that you can access if necessary.
- Ensure backup of your data
- If you are using a Martus server, ensure your records have been backed up there.
- You can also export encrypted copies of your records to local external storage, like USB sticks or an external hard drive. See Using Martus without internet/limited access for more information.
- Share safely
- Only share your information with trusted Contacts.
- Be sure to verify the public code of the Contact account you are configuring, to ensure that it matches the account public code of the person you intend to configure. This protects you against an attack where someone else pretends to be a trusted Contact.
What are the limitations to Martus security?
The Martus software uses very strong encryption technology to scramble your records so that other people cannot read them on your hard drive. However, since security involves people, and people are human, Martus security has limitations. We want to make sure you understand these limitations, even though the software is designed to be very secure. Here are some of the ways your private information may be compromised:
- Somebody can find your password written down on a slip of paper
- Your password may be too simple, such as a word or a name or a simple phrase
- Somebody may watch you enter your password, or may install a new keyboard, a special connector or special software to steal your password
- A Contact that you trusted with your key could violate your trust
- Anybody who knows your password or the password of a Contact to whom you send records could disclose that password through force, blackmail or even by accident
- Your password could be intercepted if you send it in an e-mail message, or say it on a tapped phone line
- Record attachments opened may be automatically saved in a ‘temporary’ directory which is unencrypted depending on your operating system.
- Someone could give you an altered copy of the Martus application, which could give others access to your data
- The makers of Martus could have made a mistake in designing Martus, or a scientist might invent new technology for breaking security, or enough time may pass that computers have more power to crack the security.
Although Martus has been reviewed extensively for strength of security, and computer experts can review its design to check for flaws at any time, it is likely that private information will be accessible to other parties willing to invest the time and effort to read it at some point in the future.
Although these limitations may sound scary, Martus information is far more secure than information on paper or in most existing computer programs (including those used by banks.) We explain these limitations to make sure you understand them, and the importance of being security-conscious in your use of Martus. Although we have built a very strong lock on your information, any lock can be unlocked by a key left out, and even the strongest locks can be broken with enough effort.
Creating a Strong Password
To keep your data secure, you need to use a password that cannot be easily discovered or guessed. Develop a password that you can use confidently, and that you can remember. You are the only one who knows your password; if you forget your password, you may not be able to access your Martus data (unless you have done a 3-part backup of your account, for more information see Backing up your key.)
- Do not use your username.
- Do not use just one word that can be found in a dictionary.
- Use at least 15 characters for most security (8 are required).
- Use a combination of alphabetic characters, numbers, and special characters (such as !@#$%^&*).
- Use a combination of uppercase (capital) and lowercase characters if you use a case-sensitive language.
- If you must write down your password, keep it in a secure location separate from your Martus installation.
- Create a reminder statement for yourself, and keep it somewhere secure. (Remember that if your reminder statement jogs your memory, it could also provide a clue to someone attempting to discover your password.)
- Use a password that can be remembered (use characters that are meaningful to you).
- Develop a simple method for choosing new passwords.
- Change your password if you feel that your account has been compromised. See Change your username or password for step by step instructions.
- If you forget your username or password, there is no way for you to access the records you have created or any of the data on your computer unless you have performed a multi-file key backup (or have a Contact that can retrieve your records.)
The Electronic Frontier Foundation’s Surveillance Self-Defense guide also includes good advice on creating strong passwords.
Understanding Encryption
Encryption scrambles or encodes your data so only those with the secret key or password can decode it. A very simple example to illustrate the conception of encryption:
HELLO
Algorithm: rotation
Key:2
Encrypted text:
JGNNQ
Martus uses a much more complex algorithm of encryption that scrambles the record so that it can only be read by people with the right key. Encryption protects the records easily and automatically. This is what a record looks like encrypted on your computer or sitting on the server:
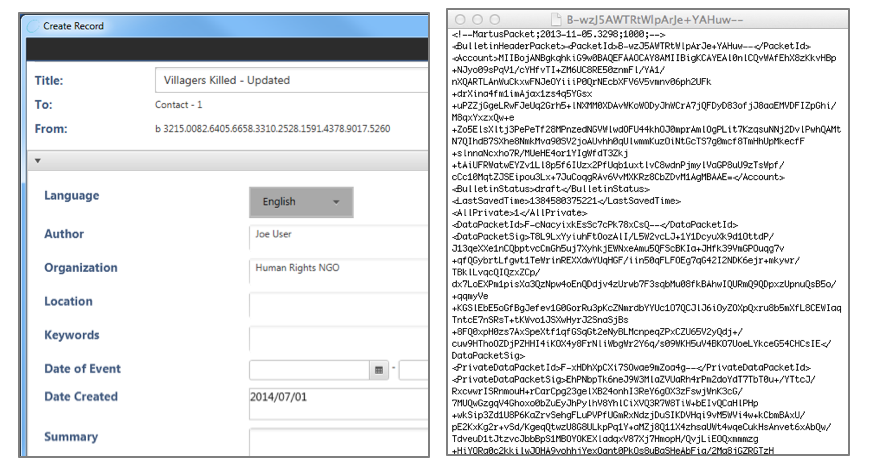
For a technical description of the encrypted used in Martus see the “About Martus Security” section, here: https://martus.org/resources/documentation.html
Other resources and examples for understanding encryption:
- Mozilla’s emoticon crypto
- Youtube videos (language options)